Cybersecurity Focus
I'm a cybersecurity-focused developer with skills in identifying vulnerabilities, mitigating threats, and implementing secure systems. My experience spans network security, secure web development, and basic penetration testing. I'm dedicated to protecting data, preserving privacy, and ensuring compliance in digital environments.
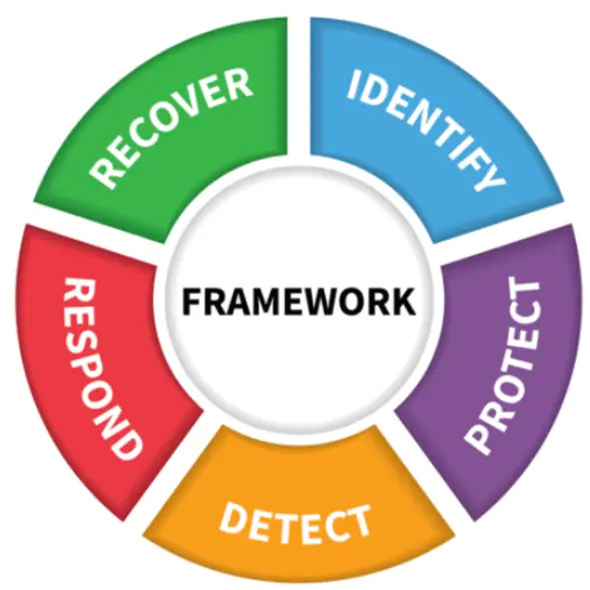
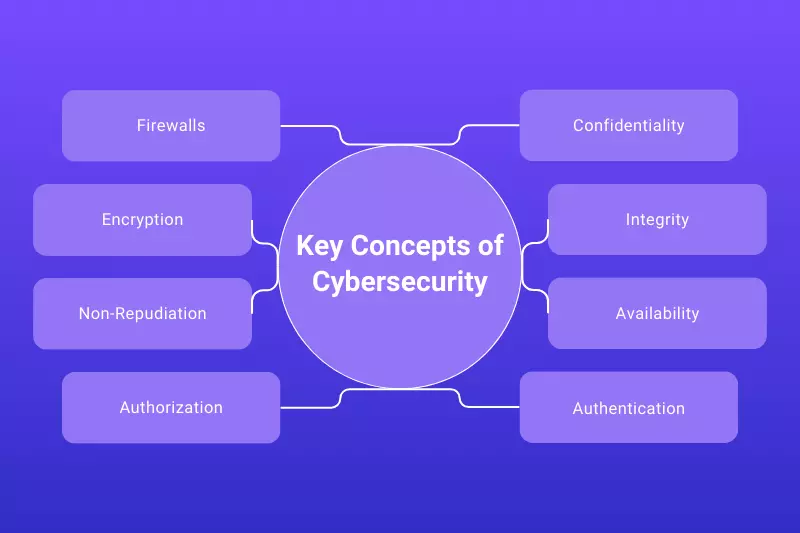
Core Security Skills
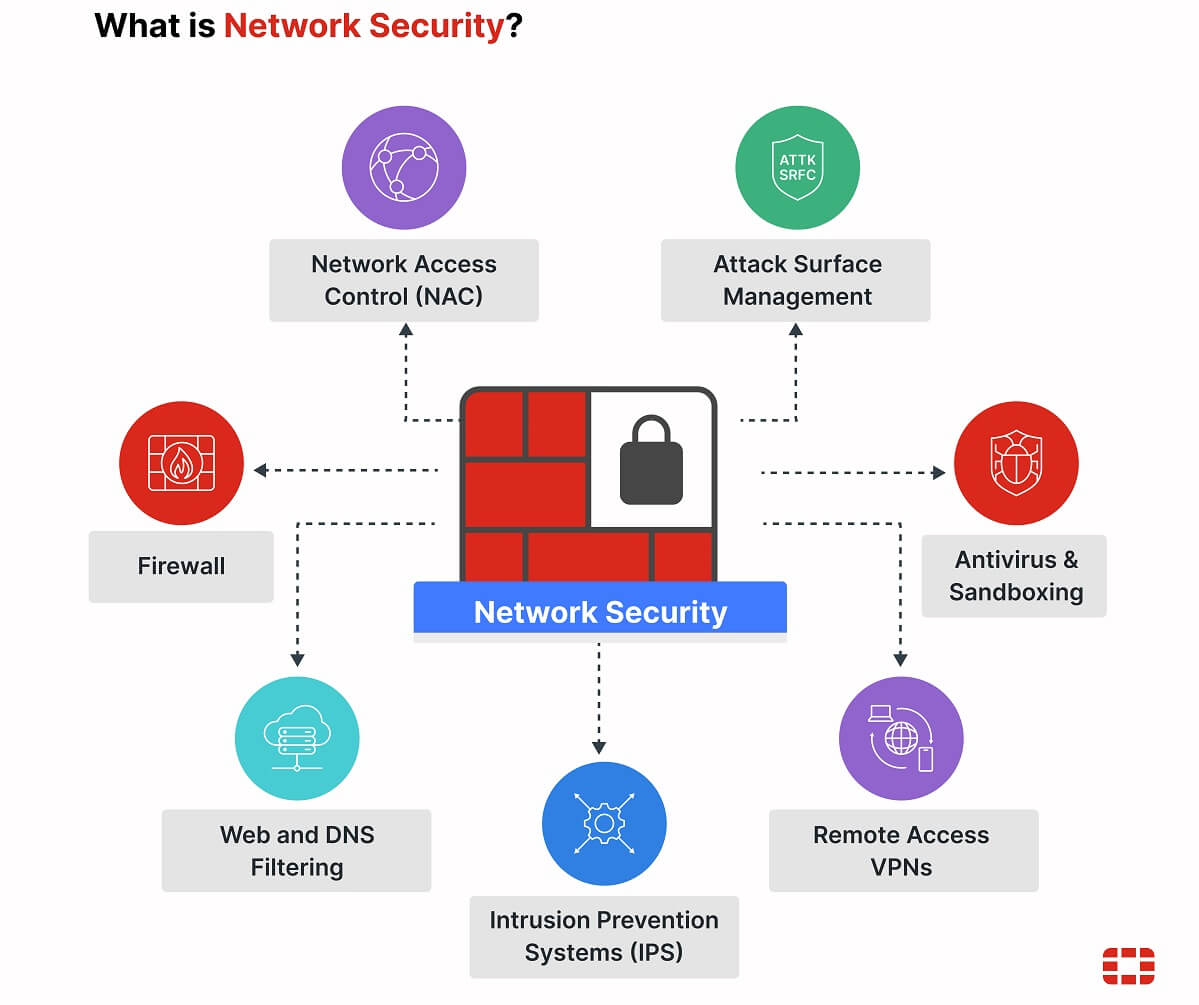
- Network and application security
- Secure software development
- Threat modeling and risk analysis
- Basic penetration testing tools (e.g., Nmap, OWASP ZAP)
- Firewall and VPN configuration
- Incident response basics
My foundation in IT and front-end development gives me a unique advantage in understanding both infrastructure and software vulnerabilities. I'm seeking opportunities where I can grow as a security professional and contribute to safe, innovative technology.